Deryck Mitchelson, Field CISO EMEA, Check Point Software.
The MITRE ATT&CK framework represents a globally accessible knowledge base containing adversary tactics, techniques, and resources designed to aid cyber security defenders. The framework empowers defenders to identify gaps in visibility, defensive tools, and cyber security processes.
It also serves as a “common language” for understanding the mechanics and impact of attacks. In turn, experts can then prepare stronger attack responses.
This article decodes the MITRE ATT&CK framework, highlights its utility and describes how to operationalize the information so that it seamlessly integrates into your existing cyber security processes and programming.
The MITRE ATT&CK framework
The MITRE Corporation is a federally funded non-profit group that receives security information from researchers, which is then catalogued in easy-to-read matrices.
The three core matrices that MITRE produces are:
Enterprise: In this matrix, users can find information covering enterprise-level preparatory techniques for Windows, macOS, Linux, cloud, network and container environments.
Mobile: In this matrix, users can see how adversaries may hack into Android or iOS devices. Individual matrices exist for each respective mobile device type.
Industrial Control Systems: Attack for Industrial Control Systems (ICS) provides tactics and technique information pertaining to ICS infrastructure. A helpful list of resources is also available to offer contextual information around ICS attacks.
MITRE ATT&CK information should not necessarily be applied directly. Some concepts or techniques may require customization in order to maximise benefits for specific organisations or projects.
MITRE ATT&CK framework’s utility
The MITRE ATT&CK framework allows for the aggregation and distribution of critical security information. Shared insights among the cyber security community can assist everyone in preparing for a more cyber secure future.
Through the active use of MITRE, security teams can prevent breaches and stop in-motion attacks. The framework can help your organisation better align security strategy with attacker behaviour, enabling you to champion meaningful and measurable security outcomes.
MITRE ATT&CK framework: Blind spots
MITRE ATT&CK’s resources primarily help defenders protect internal networks. Should your organisation need to monitor Infrastructure-as-a-Service or web applications, prioritise the adversarial techniques that need to be monitored, and conduct simulations accordingly. This will assist you in preventing the most common threats that may affect your sector or organisation.
Closing thoughts
The MITRE ATT&CK framework represents an invaluable resource for security professionals. It is open and available to any person or organization at no charge. In operationalizing the framework, you can increase your levels of threat intelligence, visibility, vulnerability management, and mitigation effectiveness.
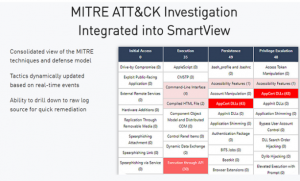
CheckPoint has integrated MITRE ATT&CK’s taxonomy into its entire solution portfolio, and in so doing, we frame attacks in a common language that the cyber community understands.
Mappings to MITRE ATT&CK techniques are included in forensic reports, malware capability descriptions, Infinity SOC and Infinity XDR, and more.
This provides an SOC analyst with a number of advantages. When analysing a particular attack, the use of MITRE ATT&CK makes it easy to understand the root causes, attack flow, and the attacker’s intent in each stage. By understanding what the attacker is trying to achieve and how, an SOC team can easily understand the scope of an attack, any necessary remediation, and how to improve defences for the future.
It’s less a question of ‘if’ your organization will experience a cyber security breach, as much as ‘when’. Incorporate MITRE ATT&CK into your security framework to augment your security effectiveness and to achieve stronger results.
Lastly, to receive more cutting-edge cyber security news, best practices and analyses, please sign up for the CyberTalk.org newsletter.




