EXECUTIVE SUMMARY:
A leak of internal documents shows that a notorious ransomware gang operates very similarly to a regular company. Workers are salaried, offered bonuses, given performance reviews and even rewarded through an ‘employee of the month’ program.
Conti ransomware gang operations
In 2021, the FBI identified the Conti ransomware gang as one of the most prolific ransomware groups known. After a recent clandestine hack, the group might now understand how it feels to be the victim of cyber espionage.
Leaked information provides insights into the ransomware gang’s size, leadership and business operations. It also revealed the group’s most prized possession; the source code for its ransomware.
Conti ransomware gang evolution
The Conti ransomware group emerged in 2020 and quickly spun itself into one of the most formidable ransomware organizations on the planet. As many as 350 people are believed to work for the group. This renders the operation significantly larger than your average Silicon Valley start-up.
Collectively, across a two-year time frame, Conti ransomware operators are believed to have brought in as much as $2.7 billion in cryptocurrency.
The critical infrastructure connection
The FBI’s Internet Crime Report 2021 reveals that Conti ransomware was among “the three top variants” that targeted critical infrastructure within the US in the last year. Critical infrastructure industries targeted included:
- Critical manufacturing
- Commercial facilities
- Food and agriculture
At present, the US is deeply concerned about critical infrastructure vulnerabilities. Read more about that issue here.
Who leaked the Conti information?
Reports indicate that it was not a US agency that disclosed information about the Conti ransomware gang.
The leaks began on February 28th, four days after Russia’s invasion of Ukraine. After the initial post, an anonymous online individual opened a Twitter account dubbed “ContiLeaks” and began pouring thousands of the group’s internal messages onto the internet along with pro-Ukrainian statements. Because the Twitter account has disabled direct messages, reporters have been unable to contact the account owner.
Says Head of Threat Intelligence at Check Point Software Technologies, the account’s owner claims to be a security researcher.
Since then, the individual responsible for the leak appears to have stepped back from Twitter. On March 30th, a post read “My last words…See you all after our victory! Glory to Ukraine!”
Conti ransomware leak impact
The Conti ransomware leak has generated extensive buzz within the cyber security community. One company has gone so far as to call the leak “the Panama Papers of Ransomware” and “one of the largest ‘crowd-sourced cyber investigations’ ever seen.”
How the Conti group works
The Conti ransomware gang is entirely “underground”. In other words, they will not make comments to news media in the way that Anonymous hackers sometimes will.
Researchers with Check Point Software note that Conti operates and is organized similarly to regular tech companies. Check Point’s Lotem Finkelstein says that Conti maintains distinctive management, finance and human resources arms. These elements are accompanied by a classic organizational hierarchy with team leaders that report to upper management.
Evidence has also emerged showing that Conti may have an “R&D” (research and development) unit.
Employee of the month program
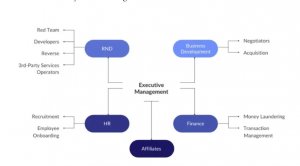
Check Point Research also discovered that Conti retains:
- Salaried employees –some of whom receive payment in bitcoin- plus performance reviews and training opportunities.
- Negotiators who receive commissions ranging from 0.5% to 1% of paid ransoms.
- An employee referral program. The referral program provides bonuses to employees who have successfully recruited others to work for the organization for at least a month.
- An “employee of the month” who is given a bonus equal to half of their salary.
In contrast with above-board companies, Conti assigns financial penalties to its under-performers.
Employee identities are masked by online handles. Examples: Stern (the “big boss”), Buza (the “technical manager”) and Target (“Stern’s partner and effective head of office operations”), according to Check Point Research.
For more on this story, click here. Lastly, to receive cutting-edge cyber security news, insights, best practices and analyses in your inbox each week, sign up for the CyberTalk.org newsletter.




